Configuration obfuscation
During SDK initialization, a configuration file is retrieved from Eppo's CDN, which includes information about the feature flag/experiment variations, traffic allocations, and targeting rules. The SDK stores these configurations locally for rapid lookup. However, when the SDK is initialized in certain mobile and browser clients, this configuration may be accessible by users, and so Eppo hashes data in the configuration to obfuscate it. The configuration cannot be hashed entirely without compromising functionality, so the hashed fields in the configuration that can be used without leaking sensitive data are shown below.
{
"flags": {
"<hashed_flag_key>": {
"rules": [
{
"conditions": [
{
"attribute": "<hashed_attribute>",
"operator": "<hashed_operator>",
"value": "<hashed_or_encoded_value>"
}
],
"allocationKey": "allocation-123"
},
...
],
"allocations": [ ... ],
...
},
...
}
}
Targeting rule values are conditionally hashed
The value field in conditions may or may not be hashed depending on the configured operator for the targeting rule in the allocation.
operator | value |
|---|---|
| is one of | hashed |
| is not one of | hashed |
| is null | hashed |
less than (<) | encoded |
less than or equal (<=) | encoded |
greater than (>) | encoded |
greater than or equal (>=) | encoded |
| matches regex | encoded |
The targeting rule's operator is configured in the UI during allocation setup.
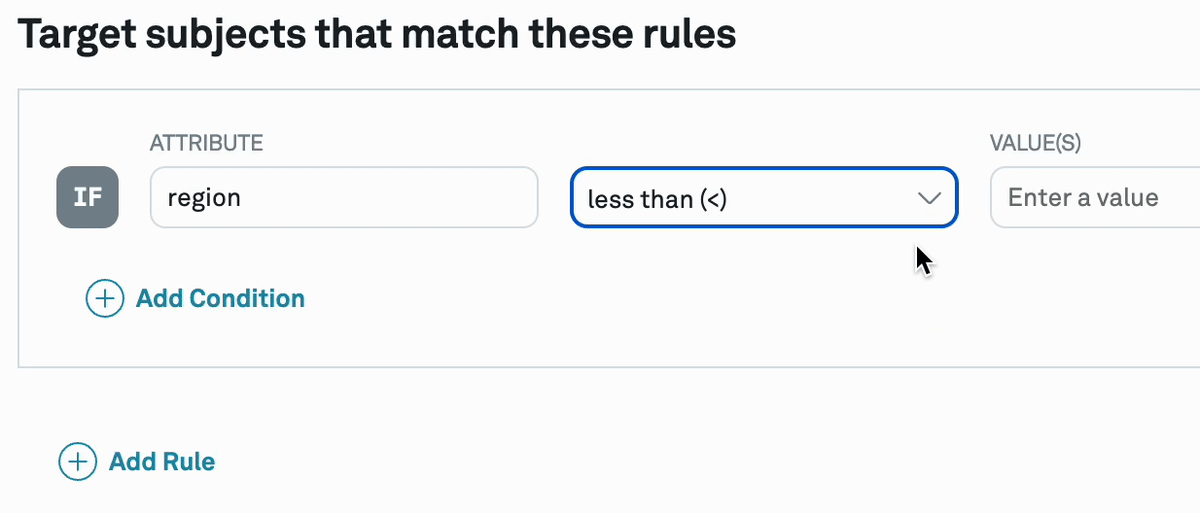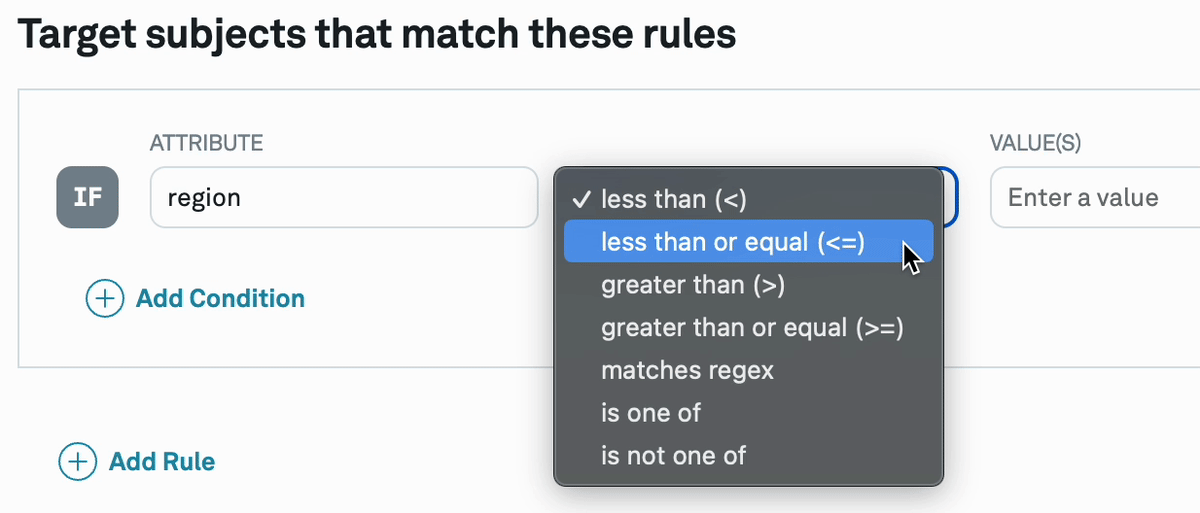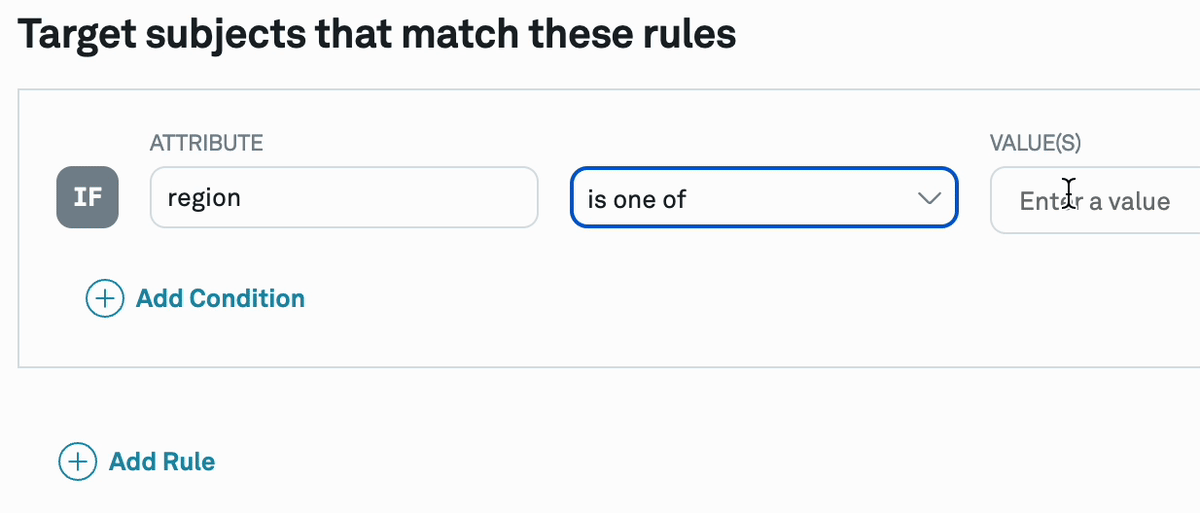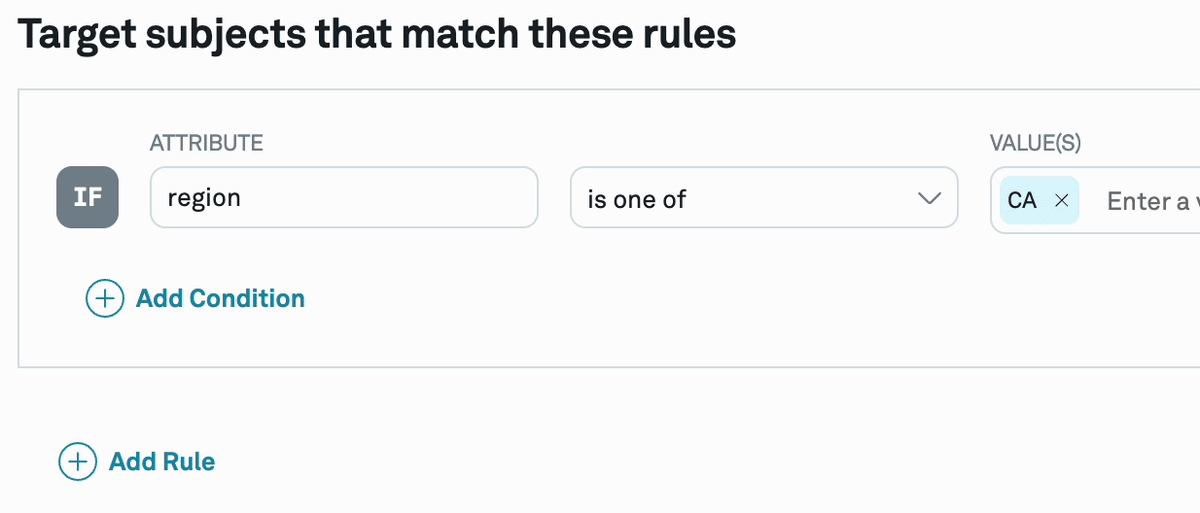
For operator types that do not support hashing, we recommend against entering sensitive data for the value.
Allocation data is not hashed
Information about allocations is not hashed, which includes percent exposure and variation names and values. We therefore also recommend against entering sensitive data when configuring variations.
Supported SDKs
| SDK | Min version | Hashed data |
|---|---|---|
| Android | v0.3.0 | feature flag key |
| Javascript | v1.3.0 | feature flag key and targeting rules |
| React Native | v1.1.0 | feature flag key and targeting rules |
| iOS | v3.0.0 | feature flag key and targeting rules |